Why Application Security Should Always Be on Your Mind
Do you know why application engineers and architects constantly think about application security? If you’ve heard the story of Samy Kamkar and MySpace, you already have part of the answer. If not, keep reading—it’s a story worth knowing.
📜 The Story of Samy Kamkar
In the early 2000s, developers focused mainly on writing code and delivering projects on time. That wasn’t wrong—but one crucial element was often overlooked: security.
A young developer named Samy Kamkar created a clever script to gain more friends on MySpace (think of it as an early version of Facebook). At first, the script ran only on his profile—but as other users visited his page, it executed automatically, sending friend requests on his behalf and copying itself across profiles.
By the end of the night, thousands—eventually millions—of users had unknowingly added Samy as a friend. This story shows how a small piece of insecure code can have massive unintended consequences.
⚠️ Why This Matters Today
Even in modern frameworks like React, security isn’t automatic. It depends on how you develop your application and for what purpose. From an architecture perspective, these areas must be addressed before you start coding:
- High-Level Architecture Diagrams
- Data Flow Diagrams
- Security Checklists
- Logging & Monitoring
🛡️ Key Vulnerabilities to Watch
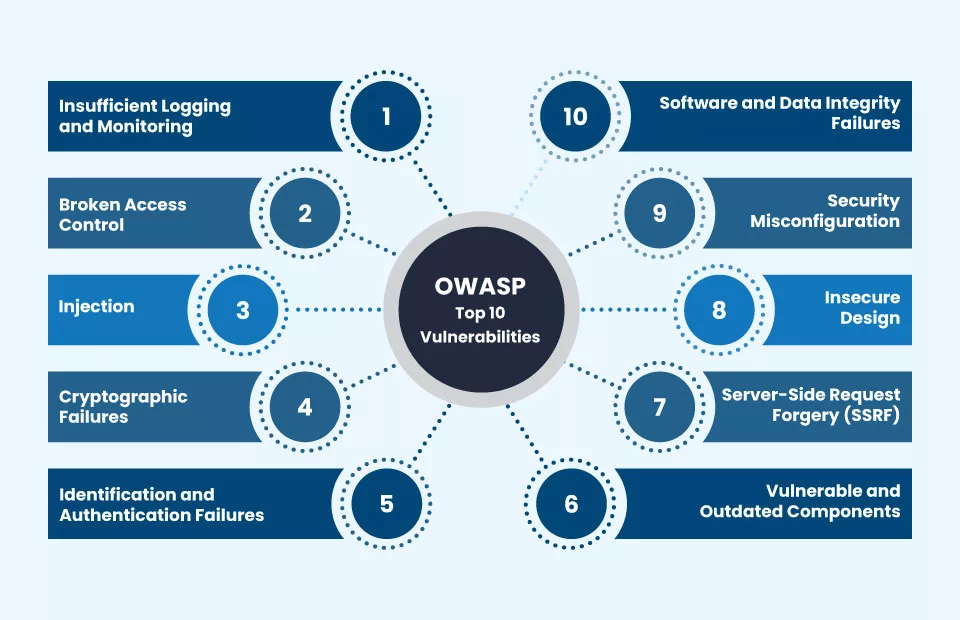
Frontend engineers should be aware of the OWASP Top 10, especially:
- XSS (Cross-Site Scripting)
- CSRF (Cross-Site Request Forgery)
- Sensitive Data Exposure
- Component Injection
- Dependency Exploits

These vulnerabilities are not just technical problems—they have created a new industry for vulnerability assessments, with tools that detect risks automatically.
💡 Recommendations for Frontend Engineers
- Design secure components and API interactions in React
- Always validate and sanitize user input
- Follow authentication & authorization best practices
- Document architecture, data flow, and security controls clearly
- Keep dependencies updated and actively monitor for vulnerabilities
📊 Example: npm Audit
Many of you have probably seen an npm audit report before. But the real question is:
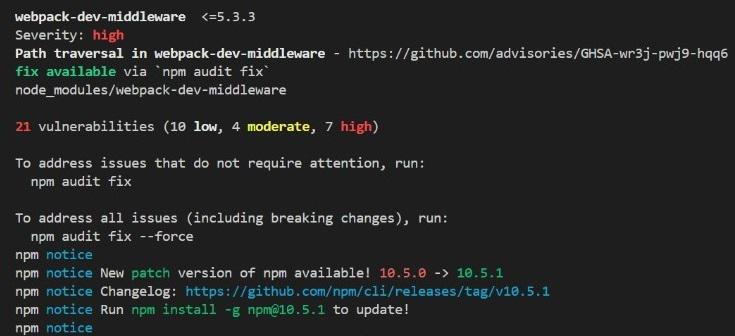
How many of us actually pay attention to it?